In this post, we are going to explore a lighweight software defined network (SDN) using Veeam PN to setup site to site VPN.
Veeam PN is a free Veeam solution that supplements the Veeam functionality of restore to Microsoft Azure and allows you to create a VPN connection between remote sites over the public network. You can use Veeam PN to implement the following scenarios:
- Set up a site-to-site VPN between company offices and a Microsoft Azure network to which VMs restored in Microsoft Azure are connected.
- Set up a point-to-site VPN between remote computers and a Microsoft Azure network to which VMs restored in Microsoft Azure are connected.
- Allow remote users to get access to a company network through a Microsoft Azure network.
Veeam PN lets you set up VPN connections between Microsoft Azure networks and on-premises networks.
The solution is based on the OpenVPN technology and features a web-based interface that simplifies VPN configuration and administration.
In the VPN, all traffic between remote networks is routed over a secure communication channel — VPN tunnel. To establish a VPN tunnel, Veeam PN uses its appliances:
a) network hub - Network hub is the core of the VPN which is responsible for traffic routing, encryption, user management, authentication and so on.
b) site gateways- is a virtual appliance that establishes a secure connection with the network hub.
Here is my lab environment simple environment:-
[Scenario 1:- Site to Site VPN]
To configure S2S VPN, perform the following configuration:-
- Deploy & configure Network Hub on Microsoft Azure
a) Network Hub Appliance in Microsoft Azure
This is how it look like after login in.
Go to Client
Click Add, select Entire Site
Enter Subnet 192.168.0.0/24 (on-premise subnet)
- Deploy and Configure Site Gateway on on-premise
b) Site Gateway
Download free Veeam PN OVA package from
https://www.veeam.com/cloud-disaster-recovery-azure.html and setup on-premise
Deploy it on-premise
Using 192.168.0.0/24 Subnet
Login to the virtual appliance using the following credential to get the ip address
- username: root
- password: VeeamPN
(use ifconfig cmd, the appliance is running on Ubuntu OS)
Use browser to login to https://veeamPN IP
Change the password
Initial configuration wizard will prompt
Select "Site Gateway"
Select the Configuration File that you've get it from Network Hub Appliance
- Add static route for outgoing traffic on default gateway
Below result indicated that our traffic is still routed to old gateway (firewall). We need to add static route for any request to 192.168.20.0/24 should route to 192.168.0.253.
Use command "route add 192.168.20.0 mask 255.255.255.0 192.168.0.253"
Perform ping test to 192.168.20.5 (Azure VM). Result from tracert showing that traffic is now route to 192.168.0.253 (Veeam PN-Site Gateway Appliance)
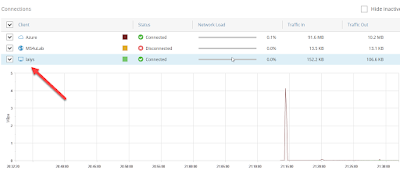
Lastly, on Veeam PN (Network Hub @Microsoft Azure) dashboard is showing traffic in and out for both network.
That's concluded on our simple test on setting up site to site vpn between on-premise & Microsoft Azure using Veeam PN.
Interested to Part 2, please refer to
here.