In this post, we are going to look into recently launched security product which using Hyper-V extensible switch and 5Nine Cloud Security. It provides agentless antivirus, compliance enforcement and traffic control/VM isolation
5Nine Cloud Security version 4 supported the following operating system:
- Windows Server 2012 Hyper-V
- Windows Server 2012 R2 Hyper-V
- Windows 8 Professional with enabled Hyper-V role
For Guest VM:- any version
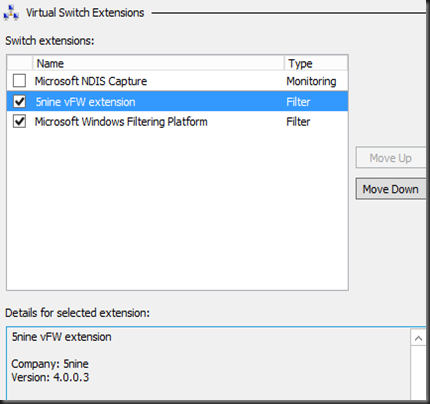
After install 5Nine Cloud Security- Host Management Service on the Hyper-V Server, you can view a new added 5Nine vFW extension on your virtual switch.
We have tested few features of 5Nine Cloud Security and here is the outcome:-
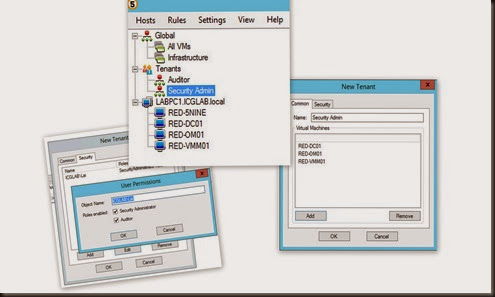
User Management and Tenants
You can set Security Administrator or Auditor permission on VM and operation through the management console. With Security Administrator, a user can be granted Full permission on the Hyper-V Cloud.
Then Auditor right allow the user to view antivirus, active protection agent, virtual firewall and IDS log but won’t able to apply any changes
Virtual Firewall
In term of virtual firewall, you can define Global rules or User Defined Groups.
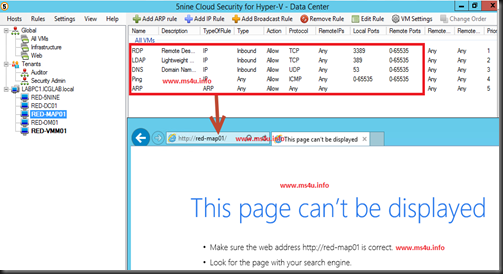
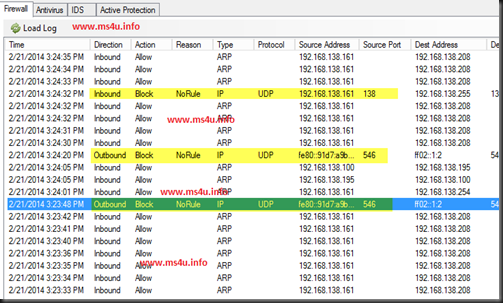
It is recommended to define a global rules first as this is the default rules apply to entire VM which are sets to use virtual firewall. In our lab environment, we have define to allow RDP, ICMP Ping , LDAP and DNS traffic to RED-MAP01 Virtual machine and block other traffics. From our test, we cannot access to webpage hosted in this VM.
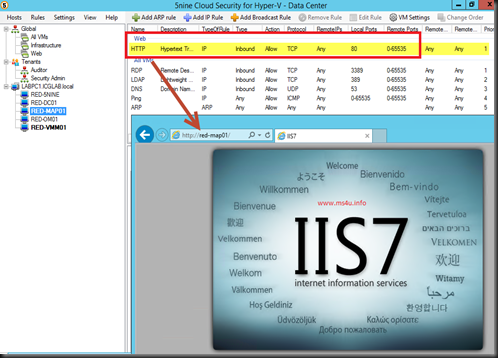
Next, is User Defined Group. These rules apply only to those VM that you assign. Remember that we want to access webpage located inside the RED-MAP01 VM. Previously we have create a global rules which block entire traffic except certain ports. Since we want to allow port HTTP so we can view the webpage, then we can create a group- Web and set to allow port HTTP. From there, you can apply that rules to RED-MAP01 Virtual machine.
From the screenshot below, a new user defined rules has added to allow inbound traffic to RED-MAP01 virtual machine. Then we was able to view the webpage after set the rules.
On the log, you also can view multiple unwanted traffic has been blocked and this ensure VMs are secured from any threat.
Antivirus
There are 2 types of how antivirus work on Cloud Security:
a) Agentless
Without install an agent into each VM, you can secure the VM by creating pre-defined schedules to run anti malware scan or on-demand an-malware scan. With version 4, it provides a fast incremental scan technology that are up to 50x faster than traditional full scans.
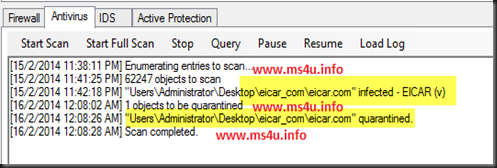
During our lab test to prove that it is fast as what they has claimed. We have ran a full scan and found no virus on 15 Feb 2014. Then we have injected “EICAR” – a test virus into one of the VM and run anti-malware scan on 16 Feb 2014. Immediately 5Nine detected the virus and quarantined it. This proved that it run an incremental scan rather than full scan to detect our test virus during on-deman scan.
b) Agent based
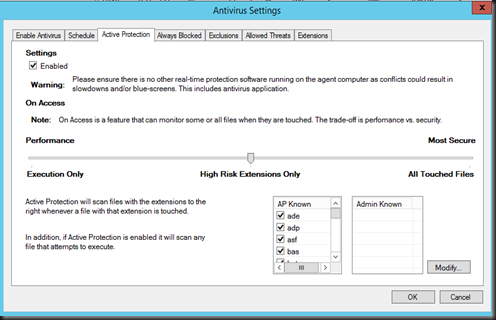
An new active protection is install to provide real time virtual machine protection including access file control.If you’ve an existing antivirus agent on the virtual machine, then we recommend that you don’t enable “Active Protection” to avoid BSOD or any potential problem.
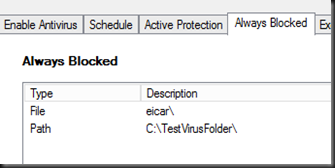
For both antivirus method, you can define virus name, folder or path to block.
5Nine Cloud Security included several exclusion to excluded from anti-malware protection and allowed on your system. This is an option for you to add your own exclusion path, files and folder.
Intrusion Detection System (IDS)
The next features which available on 5Nine Cloud Security is IDS. It is using SNORT engine to check packet anomalies that could signify potential attack to the virtual machine.
Centralize Management or SCVMM Plug-in
At this moment, it is not available during our testing. Based on the information that we receive, the SCVMM plig-in should be ready on March 2014. We will test it out and let you know the outcome when it’s release to public.
Closing…
That’s all from our testing lab evaluation. Do give it a try and see if it’s work to protect your virtualization infrastructure.
For more information, please visit 5Nine website.