You have created a virtual machine and this virtual machine has passed to another user for application deployment. Sometimes, your user tend to be smart and start to enable DHCP roles in the virtual machine which is not suppose to in your production environment. This scenario has created another rogue DHCP in your virtualization environment and you would like to prevent this from happening.
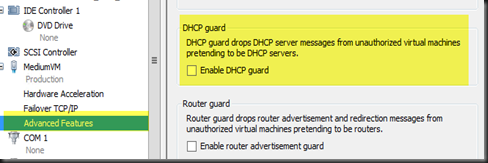
With Windows Server 2012 Hyper-V, you can prevent this by enable DHCP Guard. All you need to do is on the particular Virtual Machine Settings, Network switch tick “Enable DHCP Guard” .
Even users enable DHCP roles and it is function as unauthorised DHCP in the VM, the DHCP message will be dropped and none of the other VM will get the IP address.
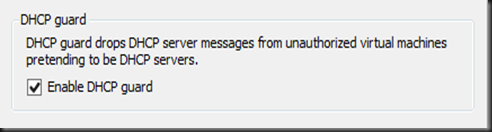
In my test environment, i have tested it with DHCP roles enabled on VM1. None of the IP is been release out to other VM when i have turn ON DHCP Guard.
To further test, i just “uncheck DHCP Guard” and it start to act as rogue DHCP and release IP to my other VMs.
Therefore, start to protect your virtualization infrastructure by configure DHCP Guard.
My recommendation on the configuration:-
| 1. Turn ON DHCP Guard for other VMs which is potential unauthorized DHCP server to prevent accidently become rogue DHCP. 2. Turn OFF DHCP Guard for an authorized DHCP server. |
Some PowerShell command to play around:-
Scenario:-
- VM1 – Rogue DHCP
- RED-DC01 – Authorized DHCP Server
| Set-VMNetworkAdapter –VMName VM1 –DHCPGuard On Set-VMNetworkAdapter –VMName RED-DC01–DHCPGuard Off |