[Updated 16 Feb 2015]
Recently we have been given an access by 5Nine to test 5Nine Cloud Security Azure Pack Extension (Release Candidate) on our WAP environment. Here is our test lab environment setup
[Preparation]
- Windows Azure Pack environment should be ready.
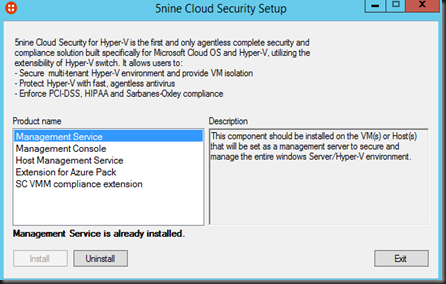
- 5Nine Cloud Security has deployed on Hyper-V environment
- Management Service & Console should deploy on a virtual machine dedicated for 5Nine
- Host Management Service deploy on each Hyper-V server
- Extension for Azure Pack deploy on WAP Portal VM
- SCVMM compliance extension deploy on SCVMM VM
[WAP – Admin Portal]
With 5Nine Cloud Security Azure Pack Extension,it provide a security solution that enables its users to manage firewall configurations and protect their Windows and Linux virtual machines.
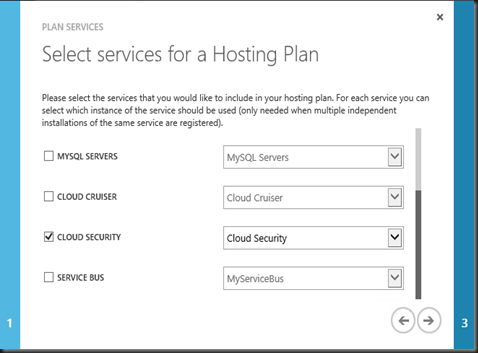
Tenant has an option to subscribe Cloud Security on their WAP Plan.
At the moment of writing the extension only include with Virtual Firewall functionality only which provide a protection to isolate VMs and control traffic. Leverage integration into the Hyper-V Virtual Switch on the host and monitor all traffic flowing to and from the VMs to provide agentless security. Click here to check out the virtual firewall features.
With the plan created and set to Public, it is time for Tenant to subscribe.
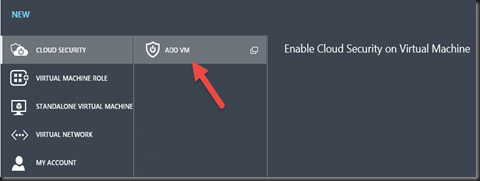
[ WAP- Tenant Portal]
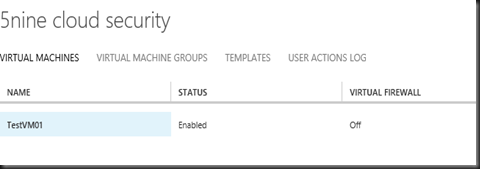
On Tenant Portal, you can enable cloud security on virtual machine that has deployed previously using WAP
By default, no rules has defined. Tenant has chance to configure security regulations themselves and increase their privacy. Now they can set up security policies, settings, and firewall rules directly through the Azure Pack portal.
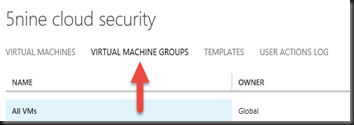
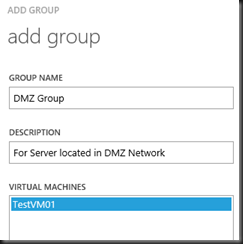
To begin with, start by creating a “User defined security group”. By default, all Virtual machine will park under “All VMs” Group which will apply default rules when enable virtual firewall. We want to apply rules to certain member of the virtual machine.
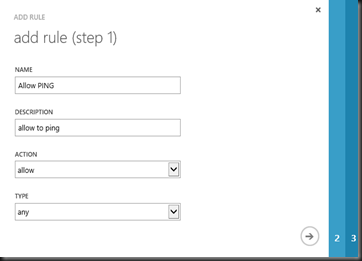
Next step is create user define template which consist a set of rules that you want to apply to group.
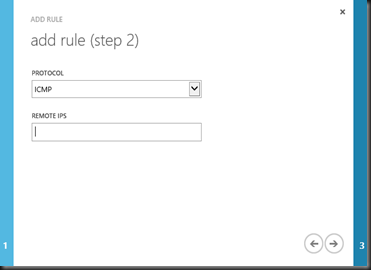
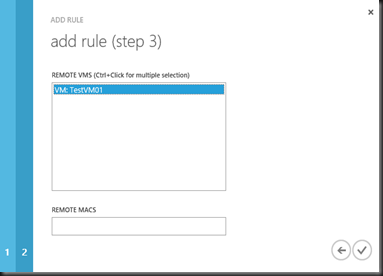
In the templates, you can start to add rules/policy to it
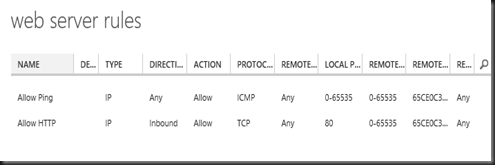
End result:-Web server rules Template
- Allow ping from any direction
- Allow HTTP from inbound connection
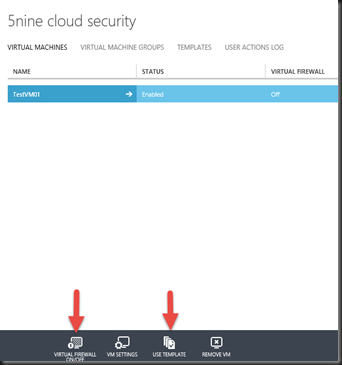
With templates created, it is time to enable virtual firewall and apply to VM. Just click on Use Template and select “Web Server Rules template” and then click “Virtual Firewall ON”
That’s all for today. 5Nine Cloud Security Azure Pack Extension is free so give it a try and test on your Windows Azure Pack environment. Good luck!
More related post:-